[2026-01-11] Deep Learning-Based DDoS Detection in SDN Networks with Explainable AI Transparency
🦥 본문
Intro
Software-Defined Networking (SDN)
소프트웨어 정의 네트워킹. control plane과 data plane을 분리하여 중앙 집중화.
- Control plane : 라우팅 테이블 생성, 네트워크 Topology 파악 등 어느 경로로 이동할 지 결정하는 부분
- Data plane : Control plane에 따라 물리적으로 패킷 전달
Architecture
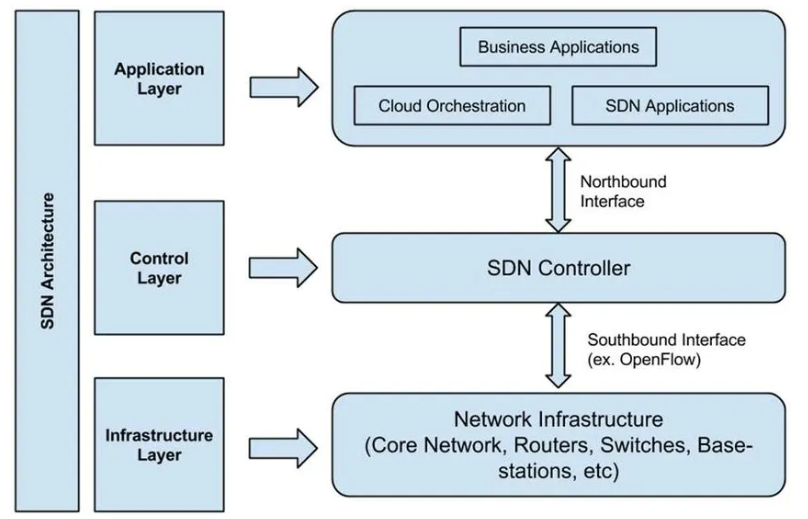
- Application Layer : 네트워크 보안, 침입 탐지 시스템(IDS), Load Balancing 같은 네트워크 서비스와 애플리케이션.
- Control Layer : SDN controller
- SDN controller : 중앙 집중적으로 네트워크 스위치를 관리
- Infra Layer : 실제 패킷 전송을 담당하는 네트워크 장비.
Interface
-
Southbound API
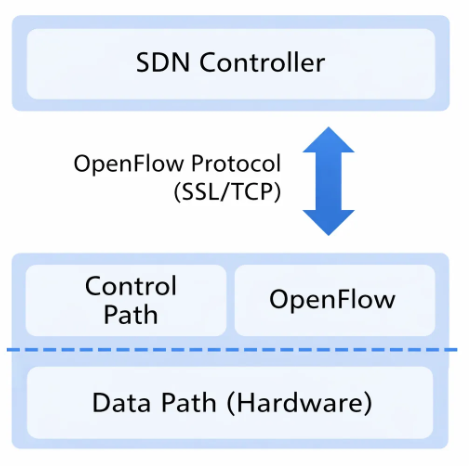
- OpenFlow 프로토콜을 사용하여 컨트롤러-스위치 통신
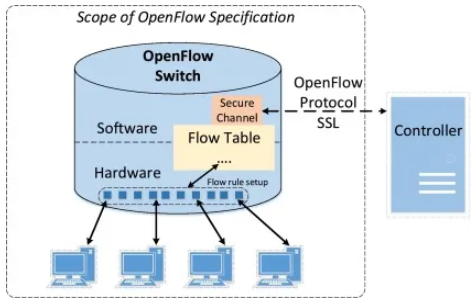
- OpenFlow 프로토콜을 사용하여 Flow table을 변경.
-
Flow table : 각 flow 마다 Rule, Action, Statistics (통계 정보)가 있음
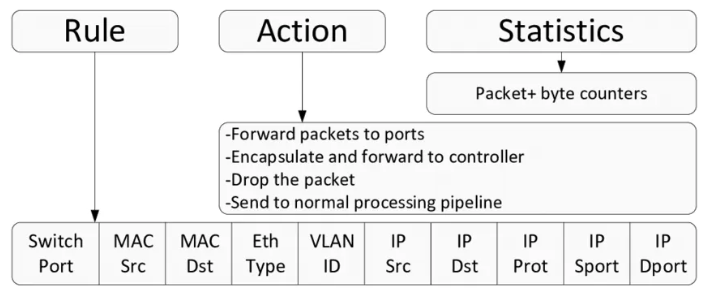
-
동작 흐름
- 네트워크에 패킷 진입
- Flow Lookup
-
여러 테이블을 통과
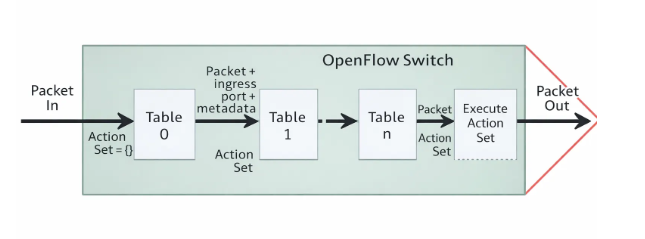
-
- table에 있는 경우 Action을 취한 후 Statistics를 업데이트
- table에 없는 경우 SDN Controller에 secure channel로 보냄
Related work
[10] : A Multi-Classifier for DDoS Attacks Using Stacking Ensemble Deep Neural Network
CNN, LSTM, GRU를 결합. 앙상블 기법을 적용. 다중 분류기 모델.
[11] : Detection of DDoS Attacks in Software Defined Networking Using Machine Learning Models
SDN 환경에서 DDoS 탐지를 위해 Random Forest, Decision Tree, Support Vector Machine (SVM), XGBoost를 포함한 4가지 알고리즘 사용
[12] : Comparative Study for Identifying and Categorizing DDoS Attacks
통계적 기법과 머신 러닝 기법. 두 가지 방법론의 강점과 한계. ML 기반이 더 성능이 뛰어난 결과를 보여줌. 이진 분류는 높은 정확도를 보여주지만 다중 분류는 정확도가 떨어짐. 또한 높은 연산 비용과 일부 연구에서는 특정 데이터셋에 의존함
[13] : Improving DDoS Attack Detection Leveraging a Multi-aspect Ensemble Feature Selection
앙상블 피처 선택 기법은 통계적 필터링 방식과 ML의 조합. 시간 단축
METHODOLOGY
데이터셋 : CIC-DDoS2019
전처리
- 일관되지 않은 값을 제거하여 무결성 보장
- 범주형 특성들은 레이블 인코딩
- Random under-sampling을 적용하여 데이터 균형
- mutual information-based feature selection을 사용하여 중요한 특성 식별
- min-max 정규화를 통해 0~1 사이로 스케일링
훈련-테스트 분할 : 테스트용 20%, 훈련용 80%
모델 : CNN, LSTM, GRU, RNN, ANN
평가 : accuracy, recall, precision, F1-score, AUC score
- AUC score : recall과 FP 사이의 관계를 나타내는 ROC 곡선의 아래 면적. 1에 가까울 수록 완벽하게 분류한다는 것을 의미
모델 설명 : SHAP는 전역/국소적 설명. LIME은 국소적 설명에 사용
Experimental results
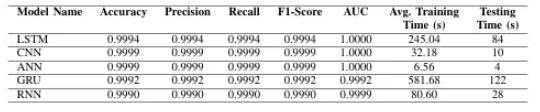
전반적으로 CNN과 ANN이 우수함. ANN이 훈련 시간과 테스트 시간이 훨씬 짧음.
-
ANN Confusion Matrix
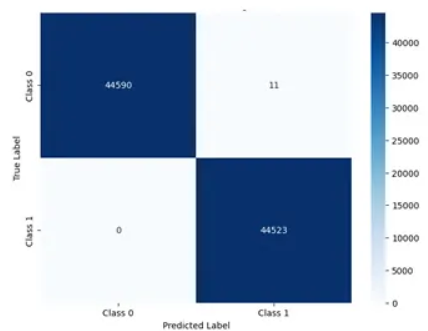
- Class 0 : 정상
- Class 1 : DDoS 공격
- 미탐의 경우가 0건
-
ROC 곡선 : 재현율과 FPR (정상인데 공격으로 예측) 사이 그래프
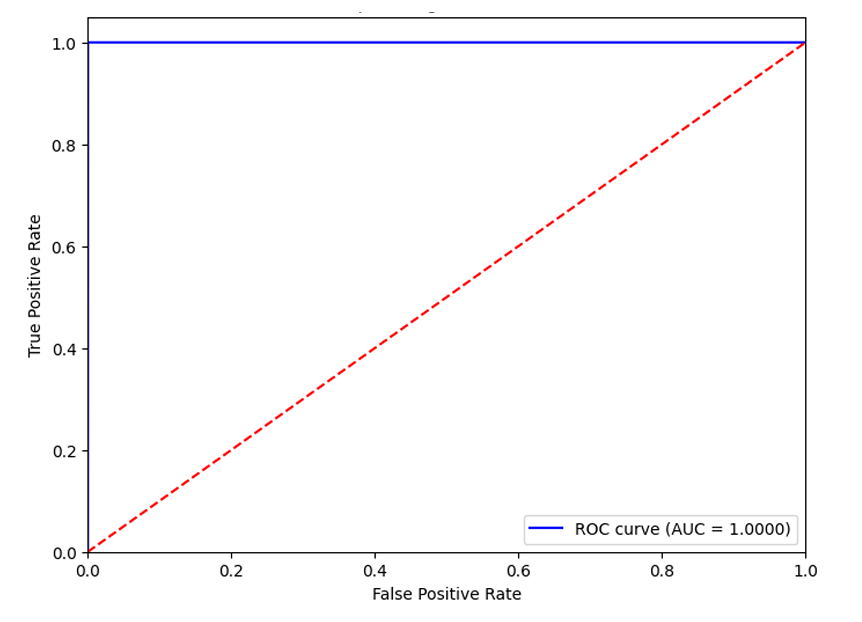
오탐이 거의 없어서 분류를 잘한다는 뜻
Comparision with Exisiting State of the Work
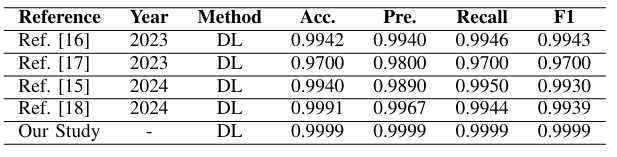
ANN 방식이 가장 좋음
Model Explanation
SHAP feature impact on model prediction of ANN
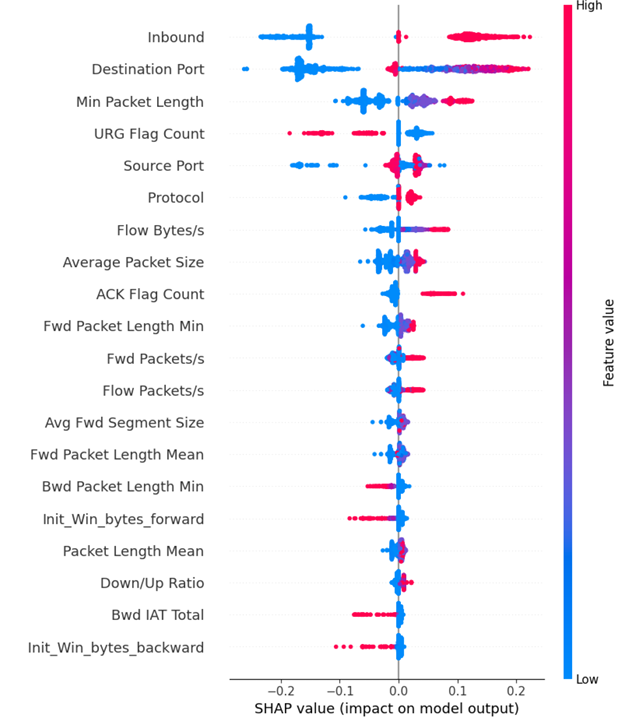
Inbound feature가 예측 결과에 가장 중요한 영향을 끼침. inbound 값이 낮을 수록 SHAP 값이 낮아지고, inbound 값이 높을 수록 SHAP 값이 증가
- ‘SHAP 값이 높아진다, 낮아진다’의 의미 : SHAP 값이 높을 수록 더 공격으로 판단. 낮을 수록 더 정상으로 판단.
SHAP waterfall plot of ANN model for a TP instance
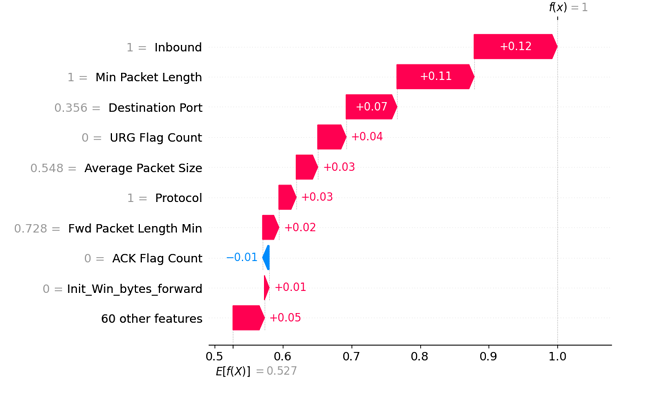
- waterfall plot : 특정 예측 결과에 대해 각 특성이 결과값을 높이거나 낮추는 데 얼마나 기여했는지 보여줌.
- 기본값 (E[f(X)]): 모든 데이터의 평균적인 예측 결과값. 그래프의 시작점.
- f(x) = 1 : 모델의 최종 결과값. 1이므로 100% 확률로 DDoS 공격
- Inbound가 1인 특성이 12%나 영향을 줌
- ACK Flag가 0인 특성이 정상이라고 생각하게 하지만 미미함.
LIME plot of ANN model for a TP instance
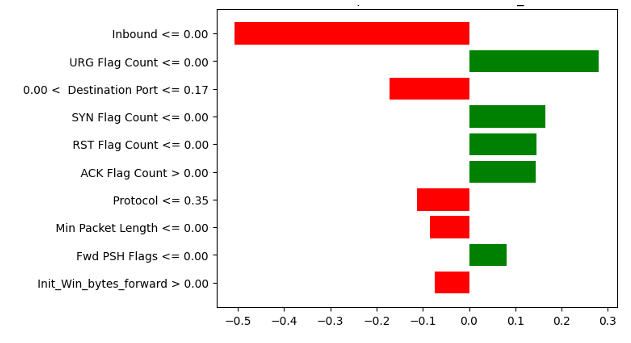 )
)
URG Flag Count가 0보다 작거나 같을 때, 가장 Positive로 분류할 확률을 높임. Inbound가 0보다 작을 때, Negative(정상)이라고 판단할 확률을 높임.
SHAP waterfall plot of ANN model for a TN instance
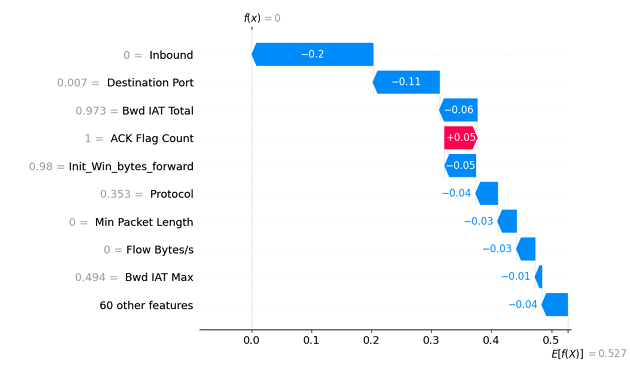
정상 트래픽 판단에 가장 큰 영향을 준 feature. Inbound가 0일 때, 정상 판단이라는 것에 20% 정도의 영향력을 끼침
LIME plot of ANN model for a TN instance
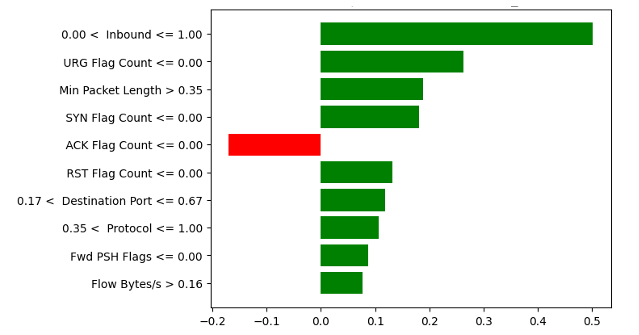
Discussion
- SDN 환경 설정에서의 효과성에 대한 실증적인 데이터는 확보 못함
- 4초도 괜찮은 건가? 데이터셋이 2019인데 최신 데이터셋에서는..?
Leave a comment